
The practical pitfalls of the EU´s ENISA 5G Security Requirements
The European Union Agency for Cybersecurity (ENISA) contributes to the EU cyber policy and specifies requirements in form of guides and regulations for 5G Security. We have seen a large range of high-quality security documents that target to improve the security of 5G. The most important ones in terms of impact for mobile network operators, vendors and cloud providers are the 5G EU Toolbox and the 5G NFV Security guide. The full range of documents related to 5G Security can be found at our blog “Impact of Securing European 5G Mobile Networks”. That list has evolved, and we are likely to see many of those measures integrated into an overarching security control matrix around the end of the year. We can also expect some further technical deep-dives.
The measures presented in those documents cover all types of deployments and service models. The effectiveness and quality of those measures against a wide range of threats is very good. The member states are taking those ENISA security documents and the contained measures and are turning them into local regulations and requirements.
That is where the practical problems start.
The 5G Toolbox can be seen as the cornerstone of 5G Security. The EU Toolbox contains strategic (SM) and technical measures (TM). The strategic measures apply mostly to the local regulator, but not only are the technical measures the duty of the mobile network operator and its partners e.g., cloud providers, service providers, managed service companies, network functions and base station vendors.
The EU 5G Toolbox in addition outlines a set of supporting actions, which support the achievement of the security objectives. The application and usage of the EU 5G Toolbox varies substantially inside the European Union. It should also be noted that the technical and strategic measures do not take into account business arrangements such as Infrastructure as a Service, Software as a Service etc. Let’s go through a two-country example, which illustrates the key problems with the adoption by the member states.
Finland is a country which has an interesting relationship with its large neighbour. Resilience of the digital society is of high importance. This is reflected in the regulations for telecommunications e.g. Regulation on information security in telecommunications operations, definition of critical network elements (Määräys viestintäverkon kriittisistä osista), Information Society Codes and related explanatory documents. Finland cooperates actively with the EU on 5G security. The requirements by the Finnish regulator Traficom directly follows the EU guidance, in particular the 5G Toolbox. In addition, the Finnish regulator also takes into account private 5G networks that are of critical importance to the society. Traficom does not go into the details of 3GPP/ GSMA Network Equipment Security Assurance Scheme (NESAS) to provide network element security. NESAS is only one potential means to fulfill the 5G Toolbox requirements to provide a baseline security to network elements. Traficom does not go into technical test cases but requires that the operator provides validated and trustworthy evidence also for the related supply chain i.e., vendors, hyperscalers etc…
Germany is a country of trade; therefore, it is not surprising that a strong emphasis is put on the security of the supply chain and standards. The BSI (Bundesamt für Sicherheit in der Informationstechnik - German Federal Cyber Security Authority) focuses on TM02 “Ensuring and evaluating the implementation of security measures in existing 5G standards”, TM07 “Reinforcing software integrity, update and patch management”, and TM09 “Using EU certification for 5G network components, customer equipment and/or suppliers’ processes” in their Technical Directive “Technische Richtlinie BSI TR-0316: Sicherheit in Telekommunikations Infrastrukturen” from May 2022. The other measures of the EU 5G Toolbox were not taken into direct use by this document. In addition to that the BSI proposes a Common Criteria (under preparation). The BSI also uses an extended German version of the 3GPP/ GSMA Network Equipment Security Assurance Scheme (NESAS) (reference Annex A of BSI TR-03163 and Network Equipment Security Assurance Scheme Cybersecurity Certification Scheme – German Implementation NESAS CCS-GI). This NESAS CCS GI extends the 3GPP specifications and adds new requirements and technical test cases. The EU Toolbox refers in their TM02 towards the 3GPP/GSMA hardening, but only as an example how to achieve a security objective. The BSI requires the NESAS CCS GI extension.
The BSI has published a list of critical network functions, if one compares that list with e.g., the Finnish list one notes that there are differences on what is considered critical in a mobile network. The differences mostly relate to RAN and some services.
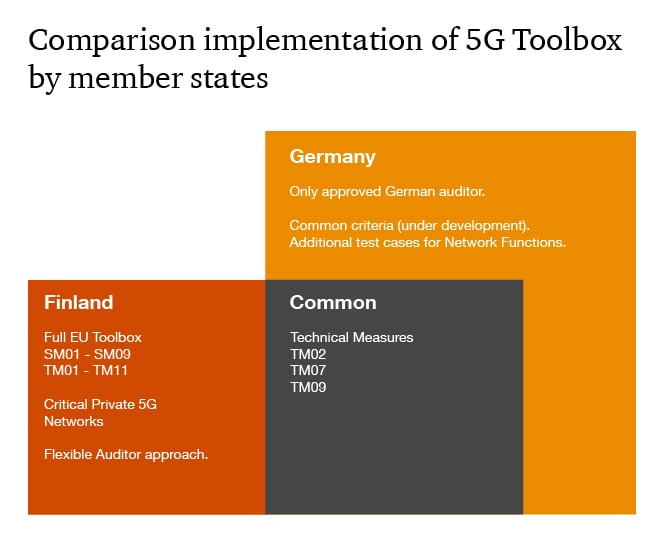
Comparison of 5G Security approach Finland / Germany
As we can see there are some overlaps on the requirements, which is good, but there are many differences in practicalities. Let’s assume that we have a vendor or cloud provider or multi-national operator. That company does not want to duplicate expensive certification and testing efforts. Also, if the certification costs are too high and the chances of entering a market are too low, then they might even refrain from making the upfront investment needed for a 5G Security certification and do not enter a market at all.
If our company now goes through the certification in Finland, then it can select any trustworthy independent auditing partner to validate the full 5G Toolbox. But that validation would not be accepted by the German BSI, as the BSI only accepts (currently) audits performed by one specific German auditing company. This implies that our company would need to run the validation of TM02, TM07 and TM09 again. In addition, the German BSI requires some extra tests due to their NESAS CCS GI usage. Other Technical Measures are covered by other German regulations e.g. the IT Sig 2.0, but the exact mapping to the EU 5G Toolbox is not straightforward.
If our company goes through the German certification, then potentially the auditing partner would be accepted. But the validation would not cover the other technical and strategic measures of the EU Toolbox, as the German government chose only some of the measures. Also, the German approach would not take into consideration “critical customers” and special protection of their private 5G networks e.g., airports, hospitals etc.
This simple example already shows the pitfalls of the EU ENISA approach. This kind of “interoperability” problem may lead to the case, where some companies do not even enter a market and by that reducing supplier choice and having a less competitive market. Also, the costs of certification will be passed down to the consumers and industry.
How to overcome that problem:
- All EU countries commit to the full EU Toolbox and 3GPP/GSMA NESAS
- Baseline definition of “critical network elements”
- Cross acceptance of a validation or elements of validation by one member state to another member state. Alternatively, a Europe wide accepted validation approach would be beneficial. The approach should not be that every member state just states that others can accept their validation. A Europe wide list of accepted trustworthy companies that can perform such validation may support this kind of interoperability.
In addition to that, each country can define their own add-ons, which can be validated separately from the EU Toolbox. This would allow that the investment made by companies into 5G security validation can be preserved and carried over into the next EU country. Hence smaller EU countries would be able to also enjoy the security benefits and the choice of suppliers that larger EU member states have. The French ANSSI (Agence nationale de la sécurité des systèmes d'information) and the German BSI have already an agreement to accept certain security certifications for telecommunication nodes (related to transport network elements like routers). This agreement is an important step to the right direction.
The new 5G security requirement approach in Europe has a very high quality, but also has many pitfalls, which are hard to navigate. We also published a blog related to the different service models between operators, cloud providers and private companies “EU 5G regulations – Impacts on operators, cloud providers and private networks”. If you have any questions, please do not hesitate to contact us.









