
Compliance for 5G and Telecommunication Cloud in Europe
5G networks are being deployed all over Europe. While 5G brings many benefits to consumers, it was primarily designed for vertical industries like production sites, logistics, cities, automotive, health care, entertainment and Internet of Things. The range of potential use cases that 5G intends to serve is very wide and also includes critical services like electricity, logistics, military and governments. To be able to cover such a wide range, 5G uses IT technologies like APIs, virtualization and cloud as key enablers for latency, bandwidth and flexibility.
Our society relies strongly on telecommunication networks already today and with 5G this reliance will increase. This fact has not been lost to the European Union and the EU’s European Union Agency for Cybersecurity (ENISA) has been strengthened in scope, personnel and mandate. In the past, national regulators focused on frequency allocation, but with 5G as a critical infrastructure that scope changed substantially. The telecommunication ecosystem is quite complex, and the radio frequency part is just a very small fraction of it. Therefore, many national regulators do not have the sufficient know-how or personnel to sufficiently cover the full scope of 5G. ENISA serves as a knowledge and resource hub for all member states to enable consistent security requirements to operators, cloud providers, vendors and service providers.
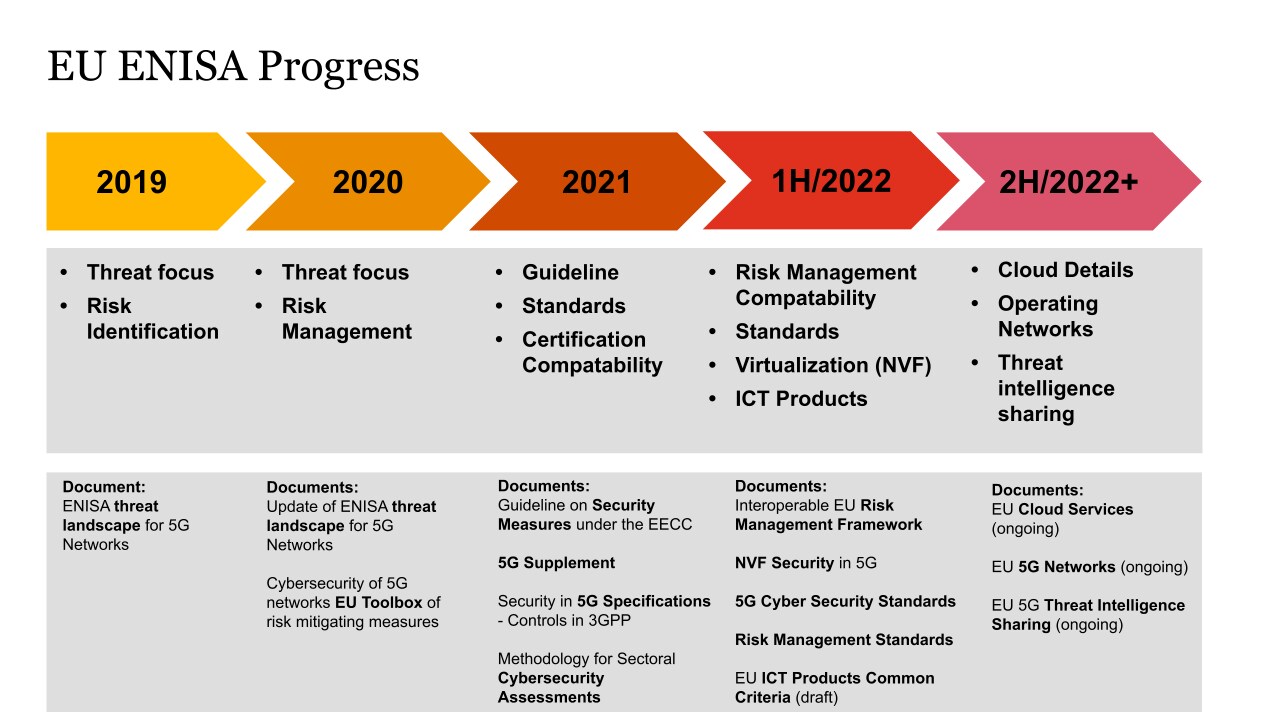
The early work of ENISA was threat analysis focused and included supply chain attacks. This then evolved into risk management and the 5G Toolbox. The need to have more specific requirements became clear and the Guideline and the 5G Supplement were published. Recently, ENISA dives into the details like virtualization and ICT products and further “deep-dives” are in the making for cloud and other topics.
The approach ENISA took is a risk management approach based on the potential threats. On the other hand, we have all kinds of business arrangements between mobile network operators, cloud providers, private networks and service providers. Each of those arrangements has different implications on the responsibilities. The elephant in the room is, who takes which responsibilities. The boundaries in mobile networks are not clear cut, due to slicing, edge servers, breakout scenarios, legacy infrastructure, roaming, mobile virtual network operators, service providers, mobility, multiple vendors, security that requires multi-layer information etc.
Some of the EU ENISA requirement documents have a very narrow scope e.g., ICT product security where the focus is on ICT vendors. Others such as the EU Toolbox, Guideline and 5G Supplement often cover all players, but to a different degree depending on the deployment approach.
While Finland is a forerunner on converting the ENISA requirements into local regulation. Some countries already have specific regulations that are extended and it is prudent to assume with the current political events that others will follow refining their regulations.
In the past, the cooperation between regulators and mobile operators centered around frequency allocation, we are now seeing a change. Regulators are responsible for ensuring the security commitments of mobile operators, cloud providers, vendors and service providers.
The recent UK government draft Telecommunications (Security) Bill gives us a taste of what may come also for the EU in terms of penalties. The current draft states that the penalty can range up to a maximum of ten percent of the mobile operator’s relevant turnover. The EU has not been shy with GPDR penalties and they seem to be serious about making sure telecommunication networks are secure. Now is the time to prepare for the application of the EU’s requirements.









